http://labs.sawbox.net/txt/ssp.html
SSP:
The Stack Smashing Protector ( SSP ) compiler feature helps detect stack buffer overrun by aborting if a secret value on the stack is changed.
by default it is included in gcc >=4.1 but not enabled, however it is distro specific
http://www.openbsd.org/papers/nycbsdcon08-pie/
PIE:
After enabling PIE support in gcc/linkers, the body of program is compiled and linked as position-independent code. A dynamic linker does full relocation processing on the program module, just like dynamic libraries. Any usage of global data is converted to access via the Global Offsets Table (GOT) and GOT relocations are added.
Ornek derleme;

gcc (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609
Copyright (C) 2015 Free Software Foundation, Inc.
Arch(enable SSP and PIE by default):

Konuya ek olarak şu güzel yazıyıda bırakıyorum;
 Stack Canary Bypass Sunucu
Stack Canary Bypass Sunucu
SSP:
The Stack Smashing Protector ( SSP ) compiler feature helps detect stack buffer overrun by aborting if a secret value on the stack is changed.
by default it is included in gcc >=4.1 but not enabled, however it is distro specific
Kod:
-fno-stack-protectorhttp://www.openbsd.org/papers/nycbsdcon08-pie/
PIE:
After enabling PIE support in gcc/linkers, the body of program is compiled and linked as position-independent code. A dynamic linker does full relocation processing on the program module, just like dynamic libraries. Any usage of global data is converted to access via the Global Offsets Table (GOT) and GOT relocations are added.
Kod:
-no-pieOrnek derleme;
Kod:
gcc -fno-stack-protector -z execstack -no-pie dem.c -o dem
Kod:
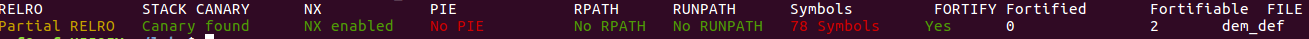
gcc dem.c -o dem_def
gcc (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609
Copyright (C) 2015 Free Software Foundation, Inc.
Kod:
Apparently Ubuntu ships version of GCC with size of buffer changed to 4,
so buffers less than that don't trigger generation of a canary.
I confirm (and anyone else should be able to repeat)
that by compiling two examples with --param ssp-buffer-size=4,
which produces assembly with canaries for only one of them.
Konuya ek olarak şu güzel yazıyıda bırakıyorum;
yinede kafana yatmayan bir şey varsa checksec, gcc version ve distro paylaşabilirsen fikir yürütebiliriz.Yazımıza geçmeden önce ben videodan daha iyi öğrenirim diyen arkadaşlar için youtube’da çektiğim videoya alalım sizleri : Video Merhaba arkadaşlar bu blogum da sizlere standart güvenlik önlemlerinden biri olan Stack Canary yani bir diğer adı ile de Stack Cookie ‘sinin nasıl bypass edileceğinden bahsedeceğim. Kafanız da güvenlik önemleri terimine ait bir yapı olmuşması için çoğumuzun bildiği bir kaç güvenlik önleminin ismini vererek yazıma başlamak istiyorum. ASLR, NX, RELRO, SafeSEH, DEP v…
